PowerRadio is a new sensor manipulation attack by injecting a malicious signal into the GND cable of the sensor and exploiting the energy conversion to interfere with and even control the sensor's measurements.
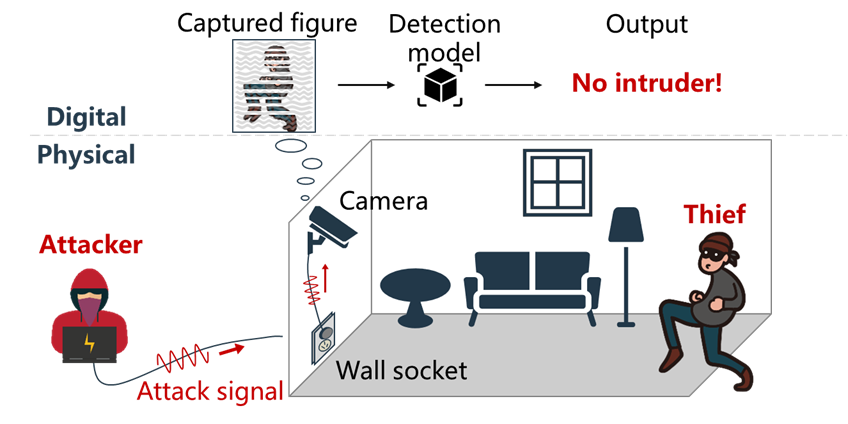
Illustration of PowerRadio in an intrusion detection scenario. An attacker injects a crafted signal into the GND port of a public charging socket, and then the signal travels through the GND wiring to the surveillance camera, inducing stripes on the captured image that can bypass the detection algorithm. Consequently, the intrusion detection system cannot detect the burglar and trigger an alert, violating the homeowner's safety.
Sensors are key components to enable various applications, e.g., home intrusion detection, and environment monitoring. While various software defenses and physical protections are used to prevent sensor manipulation, this paper introduces a new threat vector, PowerRadio, which can bypass existing protections and change the sensor readings at a distance. PowerRadio leverages interconnected ground (GND) wires, a standard practice for electrical safety at home, to inject malicious signals. The injected signal is coupled by the sensor's analog measurement wire and eventually, it survives the noise filters, inducing incorrect measurement.
We present three methods that can manipulate sensors by inducing static bias, periodical signals, or pulses. For instance, we show adding stripes into the captured images of a surveillance camera or injecting inaudible voice commands into conference microphones. We study the underlying principles of PowerRadio and find its root causes: (1) the lack of shielding between ground and data signal wires and (2) the asymmetry of circuit impedance that enables interference to bypass filtering.
We validate PowerRadio against a surveillance system, broadcast system, and various sensors.
We believe that PowerRadio represents an emerging threat that exhibits the pros of both radiated and conducted EMI, e.g., expanding the effective attack distance of radiated EMI yet eliminating the requirement of line-of-sight or approaching physically. Our insights shall provide guidance for enhancing the sensors' security and power wiring during the design phases.
Achieving PowerRadio faces two technical challenges: (1) How to effectively inject attack signals into the target sensor via power cable? (2) How to create a given output? To achieve these challenges, we present the following methods.
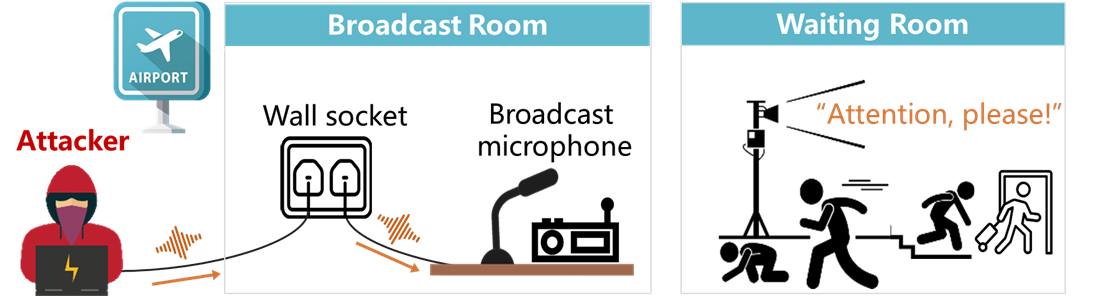
We show a demo about cross-room attack against a broadcast microphone. An attacker controls a broadcast system to play a malicious message, such as "Attention please," by injecting an attack signal into the ground (GND) port of the socket within the room.
We show a demo about motion detection sensor attack. A motion detection sensor is used to detect nearby motion, then turn on its light. As a result, the sensor will not turn on the light if there is no nearby motion. However, PowerRadio can spoof the sensor to turn on the light by injecting attack signal into the GND cable via a shared socket.
No attack: the motion detection sensor can detect the hand motion
PowerRadio attack: the attack signal interferes with the motion sensor, resulting the sensor falsely detects the motion and turns on the light even though there is no nearby motion.
Wenyuan Xu (wyxu@zju.edu.cn)
Xiaoyu Ji (xji@zju.edu.cn)
Yan Jiang (yj98@zju.edu.cn)
Yan Jiang, Xiaoyu Ji, Yancheng Jiang, Kai Wang, Chenren Xu, Wenyuan Xu. "PowerRadio: Manipulate Sensor Measurement via Power GND Radiation", accepted by Network and Distributed System Security (NDSS) Symposium. 2025.